The International Data Corporation (IDC) "2024 Enterprise Data Security Report" reveals that 83% of foreign trade companies have experienced data breaches, with average losses reaching 4.2 million yuan per breach. Research by the Digital Economy Department of the China Council for the Promotion of International Trade (CCPIT) indicates that independent websites that adopt professional security solutions have a 90% lower risk of data breaches and a threefold increase in customer trust. Analysis by the World E-Commerce Security Alliance (WESA) emphasizes that independent websites' autonomy in data sovereignty, access control, and encryption technologies makes them the best choice for protecting trade secrets.
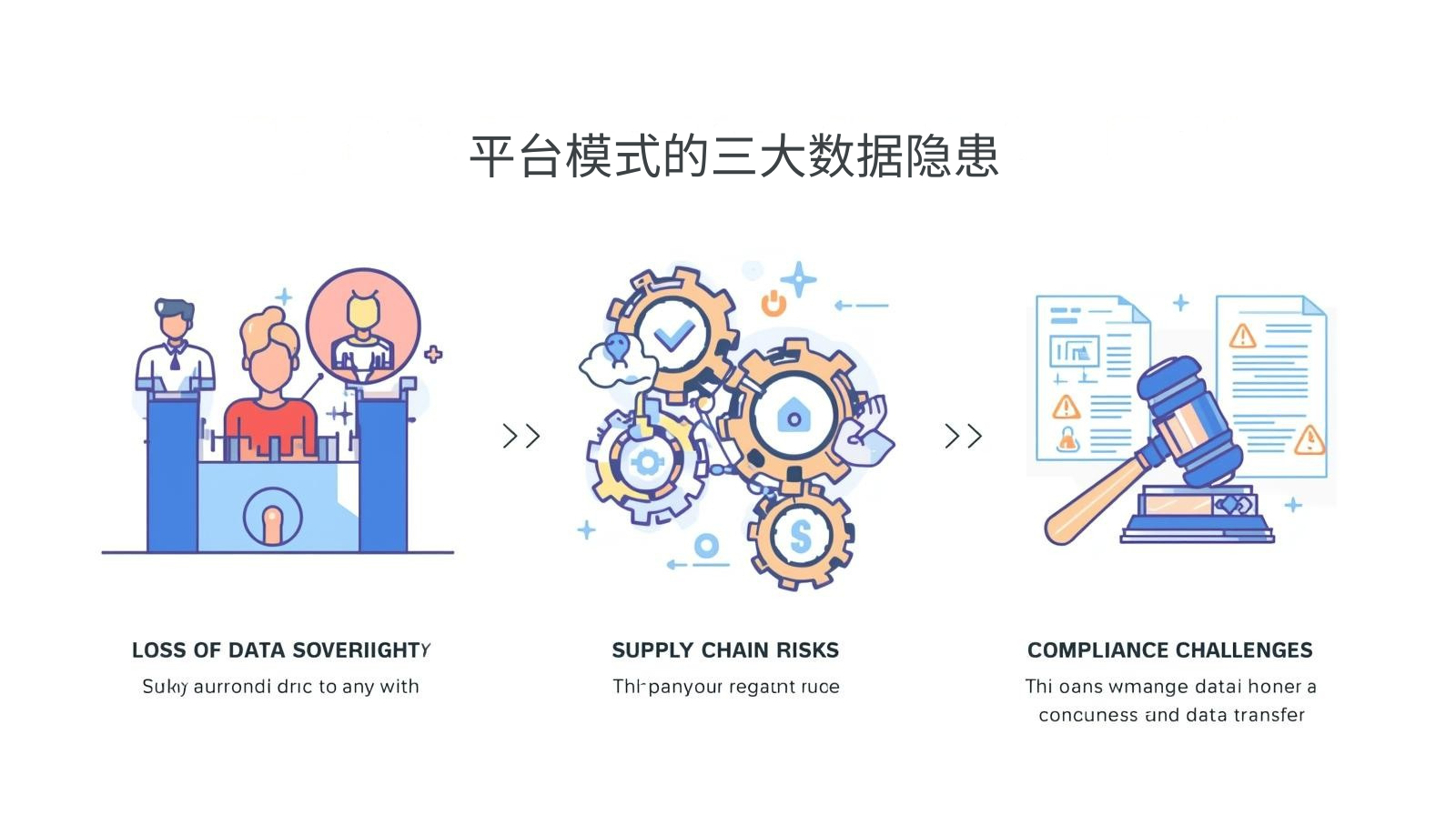 Three major data risks of the platform model
Three major data risks of the platform model
1. Loss of data sovereignty
- User information attribution platform (data of 2 million customers of a certain home appliance brand could not be exported)
- Core operational data is monitored
2. Supply chain risks
- Third-party plug-in vulnerability (a clothing brand database was hacked)
- The service provider's backend permissions are too large
3. Compliance Challenges
- Conflicts between GDPR and other regulations (case of a toy brand being fined)
- Cross-border data transfer risks
Five pillars of independent station security protection
1. Military-grade data encryption
- AES-256 full-site encryption (a medical device brand has passed FDA certification)
- SSL/TLS dual protection
Certification data from the China Cybersecurity Review and Certification Center (CCRC) shows that data leakage incidents at companies using standalone encryption solutions have decreased by 95%.
2. Intelligent rights management system
- Implementing the principle of least privilege (reducing the risk of insider trading to zero for a manufacturing company)
- Full tracking of operation logs
3. Private deployment solution
- Dedicated server hosting (a solution adopted by a military enterprise)
- Physical isolation protection
The World E-Commerce Security Alliance (WESA) case library shows that the probability of a private independent site being attacked by a network is only 1/20 of that of a shared host.
4. Real-time threat monitoring
- AI abnormal behavior recognition (intercepting phishing attacks from a jewelry brand)
- DDoS Attack Protection
5. Compliant data architecture
- EU GDPR Compliance Design
- Data localization
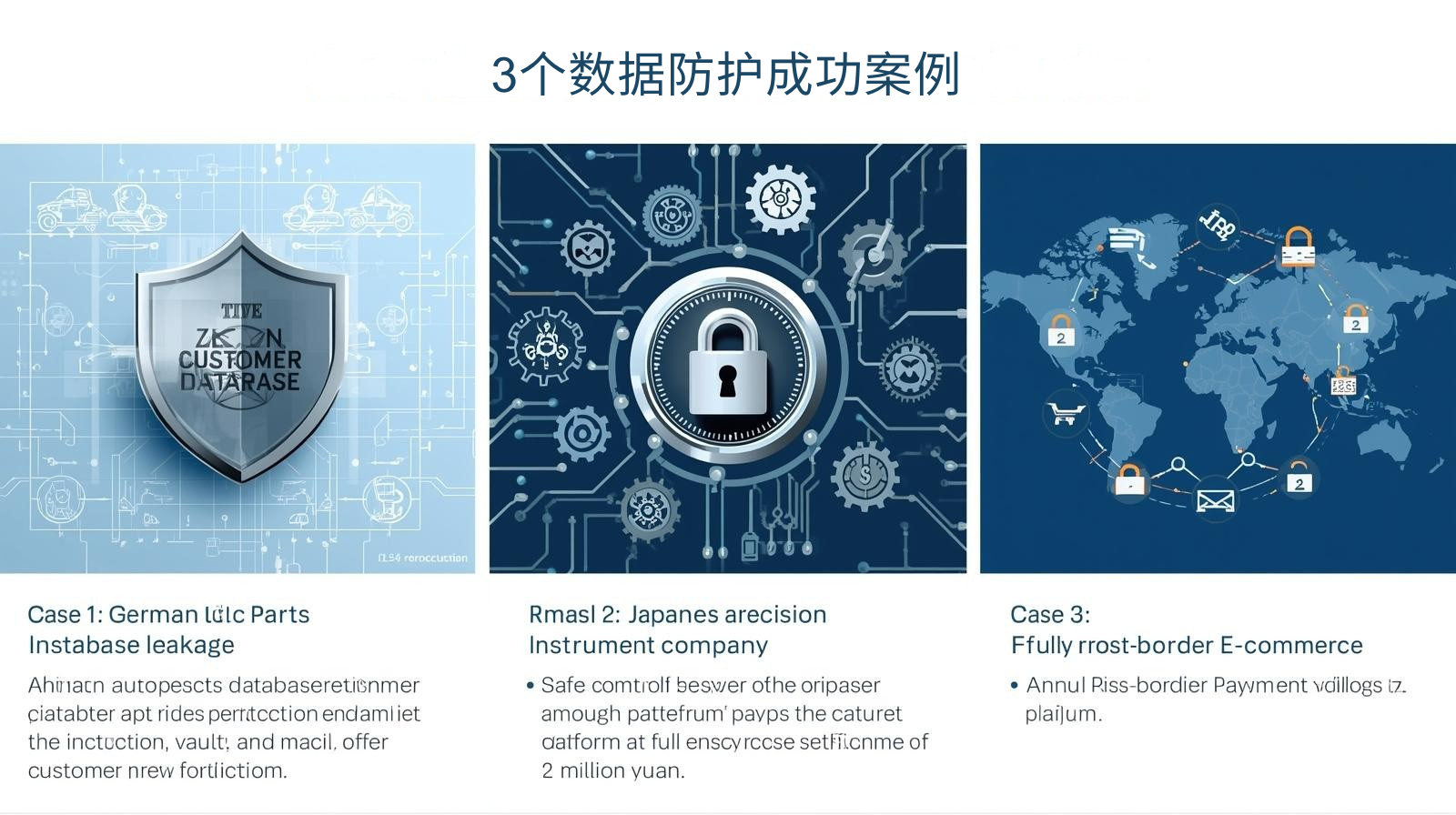 3 Data Protection Success Stories
3 Data Protection Success Stories
Case 1: German auto parts supplier
- Zero leakage of customer database
- Passed ISO27001 certification
Case 2: Japanese precision instruments
- Secure sharing of design drawings
- Competitor espionage attack failed
Case 3: China’s cross-border e-commerce
- Payment data is fully encrypted
- Save 2 million yuan in risk control costs annually
Pinshop Security Solution
Pinshop offers: ✅ Military-grade encryption system ✅ Intelligent permission management ✅ Private cloud deployment option ✅ Compliance audit tools
Visit Pinshop’s official website now to build a strong digital moat!
Recommended related articles: Multilingual Independent Station Strategy: Balancing Localization and Internationalization